Report Overview
Australia 5G Network Security Highlights
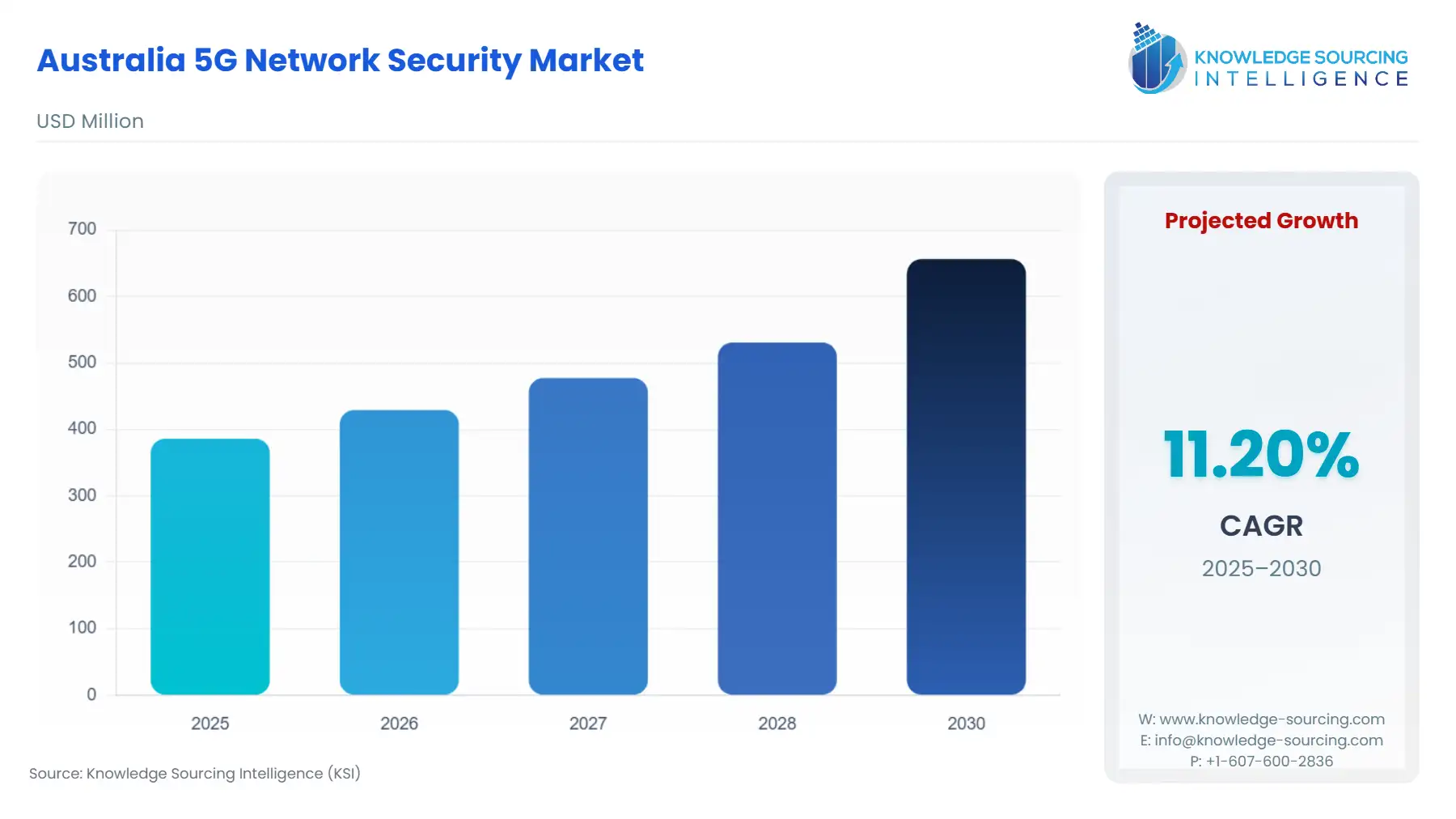
Australia 5G Network Security Market is expected to grow from USD 386.081 million in 2025 to USD 656.338 million by 2030, achieving a CAGR of 11.20%.
Australia 5G Network Security Market Key Highlights:
The Australian 5G Network Security Market operates at the convergence of aggressive infrastructure rollout and a stringent national security framework. As the Australian Mobile Telecommunications Association (AMTA) notes, 5G coverage is expanding rapidly, projected to reach 95% of the population by mid-2025, yet business adoption of the technology for transformative applications remains an emerging domain. This gap in enterprise maturity, coupled with the inherent architectural changes of 5G—specifically the shift to virtualisation and the greater reliance on the network edge—creates a sophisticated and rapidly evolving threat landscape. The market for 5G security is therefore not a derivative of general cybersecurity, but rather an integral, foundational requirement for the safe and commercially viable deployment of 5G Standalone (5G SA) and its advanced capabilities like network slicing.
________________________________________
Australia 5G Network Security Market Analysis:
Growth Drivers:
- Mandated Legislative Compliance: Mandated legislative compliance acts as a primary catalyst, directly increasing demand for security solutions. The incorporation of telecommunications into the SOCI Act requires critical infrastructure entities to implement all-hazards risk management programs, compelling immediate investment in Security Analytics & Monitoring and Security Testing & Compliance services to meet regulatory thresholds. Concurrently, the proliferation of private and industrial 5G networks in verticals such as manufacturing and mining creates a new, specific demand for Cloud Security & Virtualization Security products, as these mission-critical deployments require robust segregation and protection of virtualised network functions (VNFs) to ensure service availability and data integrity.
Challenges and Opportunities:
- Complexity of Securing Multi-Vendor Networks: A core challenge is the complexity of securing a multi-vendor, disaggregated 5G network, which constrains expansion by increasing integration overheads and requiring a higher expertise from internal security teams.
- Consulting & Integration Services and Network Slicing Security: This complexity is, however, the main opportunity for providers of Consulting & Integration services, who can address this skills gap. Furthermore, the inherent need for end-to-end security in network slicing presents a significant opportunity for security vendors. The capacity to offer intrinsic, real-time Identity & Access Management (IAM) and firewall services integrated directly into a dedicated network slice enables carriers to commercialise secure, differentiated performance-based connectivity for high-value enterprise clients, thereby expanding the demand for integrated security solutions from a capital expenditure model to an operational service offering.
Supply Chain Analysis:
The Australian 5G Network Security supply chain is globally dependent, fundamentally relying on major international technology and equipment vendors for core hardware and software components. Key production hubs reside primarily in North America, Europe, and Asia for critical elements such as advanced semiconductor chips, network security appliances, and virtualised security functions. This dependence introduces significant logistical complexities and geopolitical risk, especially given Australia's explicit national security posture regarding specific high-risk vendors. The reliance on a limited number of global technology leaders for RAN Security and core Firewalls & Threat Protection creates potential single points of failure, compelling major Australian carriers to actively diversify their vendor relationships and increasing their procurement spend on solutions from trusted sources like Ericsson, Nokia, and Cisco to ensure supply chain resilience.
Government Regulations:
| Jurisdiction | Key Regulation / Agency | Market Impact Analysis |
|---|---|---|
| Australia | Security of Critical Infrastructure Act 2018 (SOCI Act) | The Act mandates comprehensive risk management programs for responsible entities, including telecommunications providers. This drives non-discretionary demand for Security Testing & Compliance and continuous Security Analytics & Monitoring solutions to meet the legislative 'all-hazards' requirement, ensuring network resilience and integrity. |
| Australia | Department of Home Affairs (via CISC Guidance) | The 5G Security Guidance (updated in 2025) explicitly addresses Extrajudicial Direction (EJD) risk in vendor supply chains and the security convergence of the core and edge networks. This formal position directly increases the market growth for security solutions from verified, trusted vendors and drives investment in Network Encryption & VPNs to mitigate data interception risks across the network fabric. |
| Australia | Telecommunications Act 1997 (Part 14) | This framework requires carriers to protect telecommunications networks from unauthorised access and interference. It sustains a baseline, continuous demand for foundational network security solutions like DDoS Protection and perimeter Firewalls as a core operational expenditure for all Australian carriers and carriage service providers. |
________________________________________
In-Depth Segment Analysis:
By Solutions/Services: Cloud Security & Virtualization Security
The shift in 5G core architecture from dedicated hardware to a cloud-native, virtualised environment is this segment's defining growth driver. Previous generations relied on physical separation for security, but 5G's virtual network functions (VNFs) and network slicing capabilities fundamentally intermingle services on shared infrastructure. This necessitates a move from traditional perimeter security to a Zero Trust architecture, explicitly increasing demand for cloud-native Cloud Security & Virtualization Security solutions. Enterprise clients utilising private or hybrid 5G networks require assurances that their dedicated network slices are logically isolated and protected, driving investment in software-defined security solutions that secure the underlying cloud infrastructure (e.g., Kubernetes, virtual machines) hosting the 5G core. Specifically, the ability to rapidly spin up and tear down network slices requires security that is equally agile, dynamically applying security policies to individual VNFs, which can only be achieved through advanced cloud security platforms, thus fueling the market's growth. The complexity of securing the cloud-native infrastructure also converts latent demand into explicit requirements for Managed Security Services that specialise in this new, software-centric paradigm.
By End-User: Enterprise 5G Networks
The performance, deterministic connectivity, and integration of operational technology (OT) with IT boost the enterprise 5G networks segment's expansion. Industrial sectors, such as logistics and manufacturing, are adopting private 5G to enable low-latency applications like autonomous guided vehicles and real-time machine control. These mission-critical use cases cannot tolerate network downtime or data breaches, directly increasing the demand for highly reliable and ultra-secure solutions. This segment's growth is focused on intrinsic security that guarantees service level agreements (SLAs). Enterprises specifically require integrated Edge/MEC Security solutions that protect data processing at the industrial edge and Identity & Access Management (IAM) to authenticate thousands of connected IoT devices. Unlike the generic security requirements of a mobile broadband consumer, the enterprise demand is for bespoke, end-to-end security solutions that are engineered into the network from deployment, often leading to procurement of comprehensive, single-vendor security frameworks that span the RAN, transport, and core, rather than a patchwork of components.
________________________________________
Competitive Environment and Analysis:
The Australian 5G Network Security Market features a competitive landscape defined by a combination of global networking and security pure-plays and dominant local telecommunications providers. Global technology giants like Cisco Systems, Inc. and Palo Alto Networks compete intensely with core network infrastructure providers such as Ericsson and Nokia Corporation, who are positioning security as a foundational layer of their 5G stack. Australian carriers Telstra and Singtel Optus Pty Limited hold significant strategic control, acting as the primary channel to market for both consumer and enterprise 5G services. Their investment decisions and vendor partnerships directly influence the demand for specific security technologies. The competitive battleground centers on providing converged, cloud-native security platforms that offer end-to-end visibility from the device to the application, moving beyond traditional perimeter defense.
Palo Alto Networks
Palo Alto Networks occupies a leading position by focusing on a cloud-native, Zero Trust security model, leveraging its expertise in Next-Generation Firewalls (NGFWs) and SASE (Secure Access Service Edge). Their core strategy for the 5G security market involves integrating their security capabilities directly with service provider 5G networks. In March 2025, the company introduced Prisma SASE 5G, a cloud-delivered solution designed to allow service providers to rapidly integrate Zero Trust security into their 5G offerings. This product's strategic positioning enables SIM-based authentication for differentiated secure connectivity and aims to protect enterprise 5G deployments from evasive threats, directly supporting a service-provider revenue model while bolstering its competitive stance against rivals like Fortinet.
Cisco Systems, Inc.
Cisco Systems, Inc., leverages its established dominance in enterprise networking and carrier-grade infrastructure to target the 5G security domain. Their strategic positioning is centred on providing a unified security architecture that spans both the enterprise and the service provider network. Cisco offers a comprehensive portfolio, including advanced threat protection, visibility, and automation tools tailored for virtualised 5G environments. Their product strategy focuses on securing the transport, core, and cloud-native infrastructure, with offerings that integrate deeply with their networking hardware, such as the high-end routers capable of processing massive data traffic announced in October 2025, which they position as ideal for securely connecting datacenters and powering AI workloads in a distributed 5G ecosystem.
________________________________________
Recent Market Developments:
- October 2025: Cisco Systems, Inc. unveiled the Cisco 8223 router, featuring the new Silicon One P200 chip, designed to process 51.2 Tbit/s of data traffic. Cisco positioned this high-end router as ideal for securely connecting datacentres and powering next-generation artificial intelligence (AI) workloads, addressing the need for massive bandwidth and security in distributed 5G datacenter architectures.
- June 2025: Telstra successfully installed Ericsson's AIR 3284 5G triple-band FDD Massive MIMO radio into its network. This deployment, a world-first, is part of Telstra's four-year network transformation and is aimed at delivering better streaming, faster uploads, and more reliable connectivity, providing a foundational upgrade to the RAN that will underpin future security enhancements.
- March 2025: Palo Alto Networks introduced Prisma SASE 5G, a cloud-native Zero Trust security solution. This new product is positioned to enable service providers to offer end-to-end private 5G security solutions and services by leveraging a SASE cloud interconnect for fast integration into the 5G network, enhancing security for data, devices, users, and applications over 5G.
________________________________________
Australia 5G Network Security Market Segmentation:
- BY SOLUTIONS/SERVICES
- Solutions
- Firewalls & Threat Protection
- DDoS Protection
- Identity & Access Management (IAM)
- Network Encryption & VPNs
- Security Analytics & Monitoring
- Cloud Security & Virtualization Security
- Services
- Managed Security Services (MSS)
- Consulting & Integration
- Security Testing & Compliance
- Solutions
- BY DEPLOYMENT
- On-Premise
- Cloud-Based
- BY NETWORK ARCHITECTURE
- 5G Security
- RAN Security
- Edge/MEC Security
- Transport Network Security
- BY END USER
- Telecom Operators
- Government & Defense Networks
- Enterprise 5G Networks