Report Overview
Canada 5G Network Security Highlights
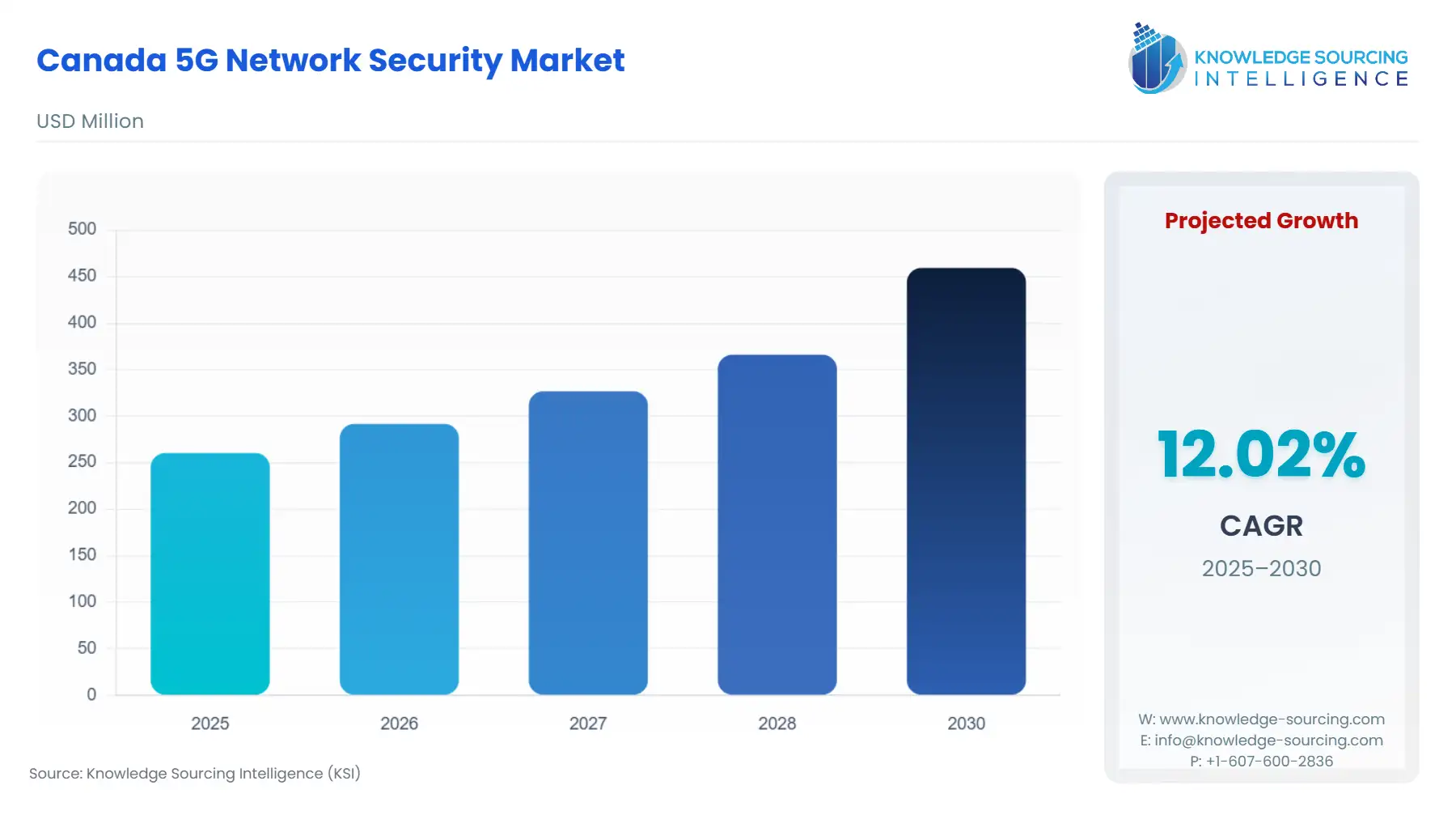
Canada 5G Network Security Market Size:
The Canada 5G Network Security Market is expected to grow at a CAGR of 12.02%, reaching USD 459.351 million in 2030 from USD 260.417 million in 2025.
The Canadian 5G Network Security market is evolving from a compliance-driven expenditure model to a strategic, performance-enabling investment. This shift is predicated on the nation's rapid deployment of 5G Standalone capabilities, which fundamentally alter network architecture by virtualizing the core and pushing compute resources closer to the edge. The resulting disaggregated, cloud-native environment, while offering immense speed and low latency, simultaneously introduces new threat vectors across the Radio Access Network (RAN), the transport layer, and the multi-access edge compute (MEC) platform. Consequently, Canadian telecommunications service providers (TSPs), alongside government and enterprise end-users, are facing a mandatory, multi-faceted security transformation. The market’s trajectory is therefore intrinsically linked to regulatory compliance, the operationalization of advanced 5G use cases, and the urgent need to secure a dramatically expanded threat surface that now spans from the central core to billions of potential IoT endpoints.
Canada 5G Network Security Market Analysis:
Growth Drivers
National 5G deployment momentum acts as the core growth catalyst. The mandated exclusion of high-risk foreign equipment from Canada’s 5G infrastructure, enforced through federal policy, immediately accelerated the demand for domestic and trusted international vendor security solutions to fill the resultant technology and capability gap. Furthermore, the commercialization of sophisticated 5G use cases, such as industrial IoT and autonomous vehicles, places non-negotiable requirements on ultra-low latency and network slicing. This necessitates security features—like dynamic network slicing security, authentication, and continuous monitoring—to be embedded within the architecture, propelling demand for security-by-design solutions that are native to the 5G core and RAN. The transition to cloud-native, virtualized core networks inherently shifts the security paradigm from hardware-centric perimeters to software-defined, zero-trust models, driving TSPs to procure advanced Security Analytics and Cloud Security solutions.
Challenges and Opportunities
A critical challenge constraining the market is the specialized talent deficit for cloud-native 5G security architecture. The scarcity of personnel proficient in securing virtualized network functions (VNFs) and containerized environments compels TSPs to outsource complex security operations, thereby directly increasing demand for high-value Managed Security Services (MSS) and Consulting & Integration services. This constraint simultaneously presents a major opportunity for global security vendors and systems integrators capable of offering fully managed and automated security platforms. Another opportunity lies in the burgeoning Enterprise 5G Networks segment; as private 5G adoption increases in critical infrastructure (e.g., ports, utilities), it creates a greenfield market for vendors to provide dedicated, customized security stacks, moving beyond the public carrier domain to directly address stringent industrial compliance and operational technology (OT) security needs.
Supply Chain Analysis
The Canadian 5G Network Security supply chain is predominantly a global, software-driven ecosystem characterized by high intellectual property (IP) concentration and limited physical component logistics, as the core products are intangible services and cloud-native software functions. The primary production hubs are dispersed globally, concentrating in the research and development centers of key American, European, and Nordic vendors (e.g., Cisco, Palo Alto Networks, Ericsson, Nokia). Logistical complexities are centered not on hardware transport but on the secure, compliant deployment of software and network orchestration tools across the Canadian TSPs' disaggregated, multi-cloud environments. The supply chain has a critical dependency on the secure provision of software licenses, cryptographic modules (often hardware-based for secure key management), and the highly skilled technical consulting services necessary for complex security system integration and deployment across 5G standalone cores and RANs.
Government Regulations
Federal government regulations are the single largest non-market-driven force shaping and enforcing demand for the Canadian 5G Network Security market.
| Jurisdiction | Key Regulation / Agency | Market Impact Analysis |
|---|---|---|
| Canada (Federal) | Policy regarding high-risk vendors (Huawei/ZTE ban) (ISED) | Direct Demand Increase: Creates immediate, non-discretionary demand for verifiable, trusted (primarily Western) vendor equipment and software to complete 5G rollouts. Forced vendors to pivot supply chains. |
| Canada (Federal) | Bill C-26 (An Act respecting cyber security) | Demand Shift & Structuring: Establishes a legal framework mandating robust security programs and incident reporting for designated 'vital services' TSPs. Accelerates demand for Security Analytics & Monitoring, and Security Testing & Compliance services to meet mandatory compliance standards. |
| Canada (Federal) | Canadian Radio-television and Telecommunications Commission (CRTC) | Demand for Resiliency: Mandates network reliability and enhanced public safety communications. Drives demand for DDoS Protection, resiliency testing, and robust network encryption solutions to ensure service continuity under duress. |
Canada 5G Network Security Market Segment Analysis:
By Technology: Edge/MEC Security
The need for ultra-low latency applications is the paramount growth driver for the Edge/MEC Security segment. The deployment of Multi-access Edge Computing (MEC) nodes shifts compute and storage resources from the central core to thousands of smaller, distributed edge locations, drastically increasing the physical and logical security attack surface. This architectural change propels demand for specialized security solutions that can enforce policy at the micro-segment level. Specifically, Edge/MEC Security is required to perform low-latency tasks such as highly granular Identity & Access Management (IAM) for IoT devices, real-time threat detection, and container security for virtualized edge applications. Traditional perimeter security is ineffective; thus, demand accelerates for security functions like distributed firewalls, policy enforcement points, and secure tunnel termination (VPNs) deployed directly on the MEC platform to isolate enterprise traffic slices from other network users while maintaining 5G's performance promise.
By End-User: Enterprise 5G Networks
The imperative for secure, high-performance private wireless connectivity in mission-critical environments uniquely drives the enterprise 5G network segment’s growth. Canadian enterprises in mining, manufacturing, and transportation require the control, reliability, and guaranteed Quality of Service (QoS) that private 5G offers for automating operations, utilizing AI-driven video analytics, and deploying massive IoT sensor networks. The security requirements for these closed networks are often higher than those of public networks, as an outage or breach can impact physical safety and critical infrastructure. This creates the need for end-to-end security stacks, including dedicated RAN security components, specialized Identity and Access Management for machines (M2M authentication), and integrated cloud security solutions for managing the private core functions. This necessity is further catalyzed by the need for regulatory compliance with industry-specific operational technology (OT) standards.
Canada 5G Network Security Market Competitive Environment and Analysis:
The Canadian 5G Network Security competitive landscape is oligopolistic, led by three major Canadian TSPs (BCE Inc., TELUS, Rogers Communications) who act as the primary customers and, increasingly, as solution providers. These carriers rely heavily on a handful of global technology and network infrastructure vendors who supply the core, RAN, and security software infrastructure. Competition among the global vendors—Cisco, Nokia, Ericsson, Palo Alto Networks, and Fortinet—is fierce, focused on establishing partnerships with the Canadian carriers to become the preferred technology partner for their respective 5G build-outs and Managed Security Services portfolios. Strategic positioning is now centered on cloud-native capabilities, zero-trust architecture adoption, and advanced AI/ML-driven security analytics that can handle 5G’s unprecedented data volumes and complexity.
Canada 5G Network Security Market Company Profiles:
BCE Inc. (Bell)
BCE Inc., operating as Bell, is strategically positioned as an end-to-end service provider, leveraging its established network infrastructure and significant capital investment in 5G expansion. Their competitive strategy centers on combining their core 5G network offering with a portfolio of business-grade cybersecurity services. Bell's positioning is to deliver a holistic solution, minimizing reliance on third-party integration by bundling its in-house security operations with the underlying network components provided by global partners. Their key product, Bell Security Edge, is promoted to secure enterprise connections and cloud services, directly addressing the demand for perimeter and cloud security as enterprises migrate workloads to exploit 5G capabilities.
Palo Alto Networks, Inc.
Palo Alto Networks maintains a strong competitive position by focusing on delivering next-generation firewall and cloud-native security platforms that align with the virtualized 5G core. Their strategy involves leveraging partnerships with TSPs and large enterprises to deploy their security solutions, such as Prisma Cloud and the 5G Security solution, across both public and private 5G domains. Their emphasis is on application-level visibility and protection across the 5G core's user plane and control plane, directly capitalizing on the complexity of securing disaggregated networks. This positioning targets the high-end demand for advanced threat prevention, Security Analytics, and Zero Trust models for 5G network slicing.
Ericsson
Ericsson’s competitive strategy is rooted in being an embedded infrastructure provider, positioning security as an intrinsic feature of its 5G RAN and Core Network platforms. Their security products, such as the Ericsson Security Manager, are designed to manage security policies and detect threats directly within the network functions. By offering security at the infrastructure layer, they directly meet the demand from TSPs who prefer security capabilities tightly integrated with the network software they already purchase. This approach facilitates compliance and operational efficiency by unifying network management and security control across the entire 5G architecture.
Canada 5G Network Security Market Recent Developments:
- October 2024: Ericsson launched new 5G Advanced software enhancements for its programmable networks. These updates target high-performing network capabilities and include critical advancements in network security and resilience features, demonstrating a push toward embedding advanced security controls and service assurance directly into the network software layer, which directly impacts the core offerings TSPs can leverage for their security portfolios.
- September 2024: Palo Alto Networks completed the acquisition of IBM's QRadar Software as a Service (SaaS) assets. This move strengthens Palo Alto Networks' security operations platform (Cortex XSIAM) by integrating QRadar's data and security operations capabilities, significantly enhancing its ability to provide AI-powered security analytics and Managed Security Services (MSS) at scale to telecommunications and enterprise customers navigating complex 5G security environments.
- February 2024: Palo Alto Networks launched its Private 5G Security Solutions with an expanded partner ecosystem. This move provides end-to-end security for enterprise-specific private 5G deployments, addressing the growing demand for dedicated security stacks in critical industry sectors. The solution’s focus on the entire private 5G lifecycle, including deployment, management, and secure access, directly fuels the Enterprise 5G Networks segment.
Canada 5G Network Security Market Scope:
| Report Metric | Details |
|---|---|
| Total Market Size in 2026 | USD 260.417 million |
| Total Market Size in 2031 | USD 459.351 million |
| Growth Rate | 12.02% |
| Study Period | 2021 to 2031 |
| Historical Data | 2021 to 2024 |
| Base Year | 2025 |
| Forecast Period | 2026 – 2031 |
| Segmentation | Solutions/Services, Deployment, Network Architecture, End-User |
| Companies |
|
Canada 5G Network Security Market Segmentation:
- BY SOLUTIONS/SERVICES
- Solutions
- Firewalls & Threat Protection
- DDoS Protection
- Identity & Access Management (IAM)
- Network Encryption & VPNs
- Security Analytics & Monitoring
- Cloud Security & Virtualization Security
- Services
- Managed Security Services (MSS)
- Consulting & Integration
- Security Testing & Compliance
- Solutions
- BY DEPLOYMENT
- On-Premise
- Cloud-Based
- BY NETWORK ARCHITECTURE
- 5G Security
- RAN Security
- Edge/MEC Security
- Transport Network Security
- BY END USER
- Telecom Operators
- Government & Defense Networks
- Enterprise 5G Networks