Report Overview
Network Security Market - Highlights
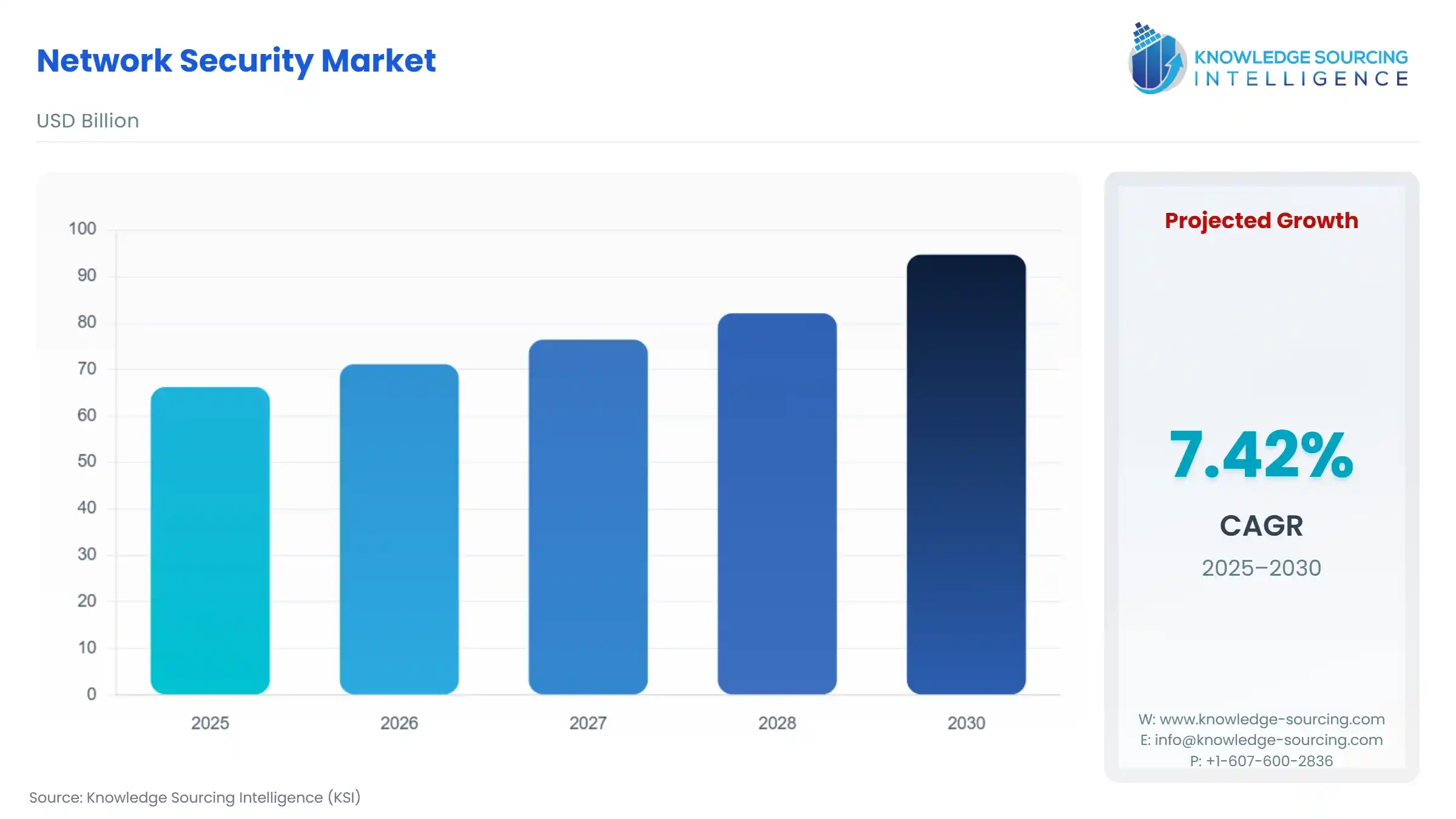
Network Security Market Size:
Network Security Market, with a 7.2% CAGR, is anticipated to reach USD 100.506 billion in 2031 from USD 66.235 billion in 2025.
Network Security Market Trends:
The network security market is estimated to grow at a constant rate during the forecast period. Network security entails the strategies and procedures put into action to obstruct, identify, and scrutinize unauthorized entry, abuse, alteration, or restriction of access to a computer network and its accessible resources. The network security market growth is propelled by several key elements, such as the escalating frequency of cyber-attacks on networks, the widespread adoption of 5G networks, and the emergence of remote work trends.
Network Security Market Drivers:
Increasing cyber-attacks bolster the network security market.
Network security is leveraged to protect computer networks and their accessible resources from unauthorized access and misuse of service. The lack of cybersecurity measures and the growing IoT devices, all of which present new vulnerabilities, have propelled cyber-attack incidents. This escalating cyber threat landscape, along with stringent data protection regulations, is fuelling the growth of the network security industry. According to the report provided by Check Point Software, the incidence of cyberattacks globally has surged, witnessing a rise of 38% per week on corporate networks in 2022, as compared to the figures from 2021.
Adoption of 5G networks drives the network security market expansion.
The technological leap facilitated by 5G, enabling a massive increase in the volume of data exchanged and the speed of its exchange, dramatically escalates the potential risks posed by cybercriminals. These accelerated, extensive networks require robust, comprehensive protection to safeguard them against potential breaches, unauthorized access, data theft, and other cybersecurity threats. Therefore, the global expansion of 5G technology has intensified the demand for top-tier network security solutions to ensure the integrity, confidentiality, and availability of data across these rapidly evolving networks. For instance, in October 2022, the Indian government took a significant step towards the nationwide implementation of 5G services by introducing an indigenous 5G Non-Standalone (NSA) Core. This cutting-edge technology, developed by the Centre for Development of Telematics (CDoT),
Emerging remote work trends drive network security market growth.
Network security is used in remote work scenarios for protecting the integrity and confidentiality of data transmitted across networks, as well as guarding against unauthorized access to systems. This increase in remote work due to the global pandemic and subsequent realization of its convenience and cost-effectiveness has increased the potential of cyber threats, including devices and networks that may not have the same security measures as the traditional office environment. As such, the heightened vulnerability has necessitated the strengthening of network security, thereby fuelling the growth of the network security industry. For instance, according to the survey conducted by the Tokyo Metropolitan Government, in 2022, approximately half of the companies situated in Tokyo embraced telework, while 20% of the employee force worked remotely.
Network Security Market Geographical Outlook:
North America is predicted to dominate the network security market.
North America will hold a significant share of the market due to significant government investment and initiatives aimed at strengthening the nation's defense against rising cyber threats, simultaneously stimulating advancements in network security technology. For instance, in May 2021, the Canadian government invested $80 million directed towards bolstering research and development in cybersecurity at enhancing cybersecurity infrastructure. Furthermore, acquisitions and collaborations by major companies in the region also play a substantial role in this growth. For instance, in March 2023, Hewlett Packard Enterprise strengthened its network security capabilities by acquiring Axis Security, a provider of Security Service Edge solutions.
Network Security Market Restraints:
Expensive solutions may restrain the network security market growth.
The financial implications associated with the implementation of advanced network security solutions can often be substantial, creating a potential barrier to their adoption, particularly amongst small and medium-sized enterprises (SMEs). These organizations may not have extensive financial resources allocated specifically for cybersecurity measures, causing them to hesitate in adopting high-cost solutions. For instance, the baseline costs for outsourced cybersecurity services typically range from approximately $2,000 to $3,500 monthly. This significant investment might be prohibitive for SMEs operating on tight budgets, thereby potentially hindering the widespread adoption of these necessary security measures.
Network Security Market Company Products:
Cisco Secure DDos: Cisco provides a network security solution known as Cloud DDoS. This service is designed to protect networks from Distributed Denial of Service (DDoS) attacks, which can overwhelm a network with unwanted traffic, causing interruptions or complete shutdowns. By leveraging the cloud, Cisco's solution offers robust and scalable protection to ensure the continuity and security of network services.
X-Force Threat Intelligence: IBM's X-Force Threat Intelligence is a cloud-powered platform that empowers users to effectively engage with, disseminate, and respond to threat intelligence. It provides users with the ability to swiftly investigate the most recent worldwide security threats, accumulate actionable intelligence, seek expert advice, and collaborate with fellow professionals. This platform not only offers comprehensive insights into cybersecurity threats but also facilitates a proactive response to potential cyber threats.
List of Top Network Security Companies:
Cisco
Fortinet, Inc.
Trellix
IBM
SonicWall
Network Security Market Scope:
| Report Metric | Details |
|---|---|
| Study Period | 2021 to 2031 |
| Historical Data | 2021 to 2024 |
| Base Year | 2025 |
| Forecast Period | 2026 – 2031 |
| Companies |
|
Report Metric | Details |
Network Security Market Size in 2025 | USD 66.235 billion |
Network Security Market Size in 2030 | USD 94.724 billion |
Growth Rate | CAGR of 7.42% |
Study Period | 2020 to 2030 |
Historical Data | 2020 to 2023 |
Base Year | 2024 |
Forecast Period | 2025 – 2030 |
Forecast Unit (Value) | USD Billion |
Segmentation |
|
Geographical Segmentation | North America, South America, Europe, Middle East and Africa, Asia Pacific |
List of Major Companies in the Network Security Market |
|
Customization Scope | Free report customization with purchase |
Network Security Market Segmentation
By Component
Solutions
Firewall
Intrusion Prevention System (IPS)
Network Access Control (NAC)
Antivirus Software
Others
Services
By Deployment
Cloud
On-Premise
By Enterprise Size
Small
Medium
Large
By End-User
BFSI
IT & Telecommunication
Government & Defense
Retail
Manufacturing
Others
By Geography
North America
USA
Canada
Mexico
South America
Brazil
Argentina
Others
Europe
Germany
France
United Kingdom
Spain
Others
Middle East and Africa
Saudi Arabia
UAE
Others
Asia Pacific
China
India
Japan
South Korea
Indonesia
Thailand
Taiwan
Others